Very Dangerous Alert
Hello dear readers, I hope you are doing well during 2020...
After a long break with no posts, i would like to show you some interesting phishing campaign i have recently seen.
I will start with the email headers, as they are somewhat interesting, but i wont comment on them as this is not the main point of this blog :)
The email is allegedly sent from support@paypal.co.il which is legitimate address, but it has been "spoofed" in the headers as partially seen in figure 0.
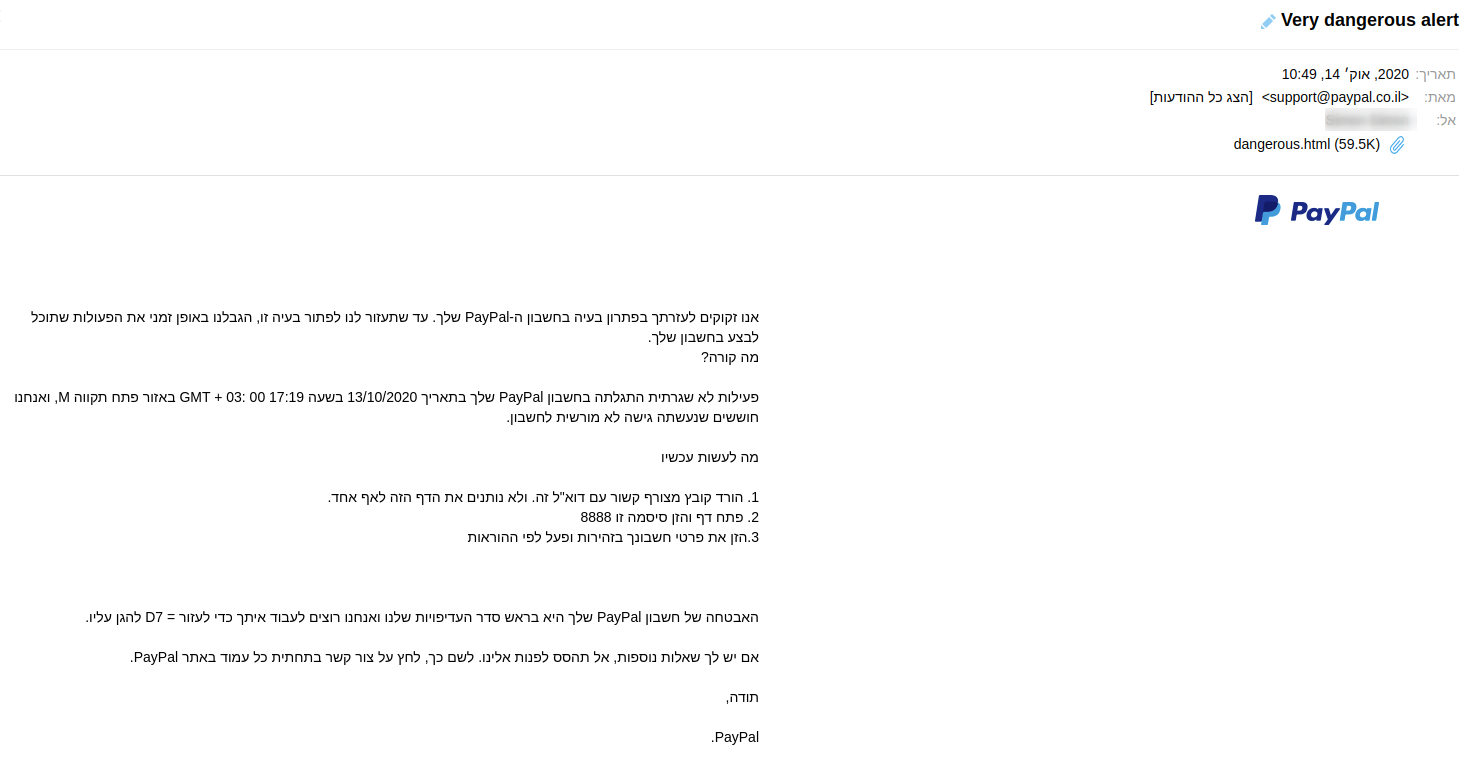
The mail is written in grammatically broken Hebrew, the title is in English though.The mail contains an HTML attachment, nothing new here, known tactic, the mail doesn't have any links to URLs so the mail is less likely to be flagged by Email security products.
The interesting part which made me write this post is the fact that the broken Hebrew text says the file is password protected with the password 8888
Password protection on HTML??? This made me curious how the attackers implemented this password protection :P (spoiler alert! you can enter almost anything to view the page)
As can be seen in figure 2, this actually look like a simple JavaScript implementation, lets check the source:
As can be seen in figure 3, this is indeed JS implementation :)
First, there is a function to get the "secure" password, named "get_password".
After that, there is a big chunk of junk which is "secured" by JS unescape function.
I would give that code as an interview question, simply because this is some math nonsense, first semester CS stuff...
Why on earth the attacker does modulus operation between orig.length & pass.length ???
Since I hate math and I am too lazy to debug the code at the moment, I will leave this as an exercise for the reader to figure out what is happening, feel free to write a comment with your observations :)
I will only say this, if you enter 8888 the page renders correctly, if you enter anything else except blank password, the swap operations in the red rectangle (figure 4) will add wrong HTML code and the page might render a little broken, or in some cases, it will be totally unreadable:
I did some basic de-obfuscation in the browser console to reveal the URL that the credentials are being sent to: http://alexander147.domain.com/f.php (Hi headers!)
I personally haven't seen until now this "password protection" technique used on phishing until now.
My memory is very selective, therefor i like to write seemingly non-sense like this post for future reference. During the writing of this blog i started to think again if i saw A password protection on phishing page.
If i did encounter a phishing page in the past with password protection, it sure did have a working mechanism, so i wasn't triggered to write about it :)
In conclusion, this is your everyday paypal phishing kit with a twist, not very very dangerous at all :/
HTML file: https://www.virustotal.com/gui/file/54609d2c5318853ef31ad282970635651f00e0a2f107987028f684f0a3a47a1b/detection










Comments
Post a Comment